How to secure REST APIs? What is difference between rest and API? You can use one of the following methods: Attaching Oracle Web Services Manager (OWSM) policies.
Protect your server against SQL or NoSQL injection attacks. Session Based Authentication. No Sensitive Data in the URL. Restriction on Method Execution.
The GET method should not be able to delete data. The calling client can perform predefined operations using the Restful service. Every time you make the solution more complex. By always using SSL, the authentication credentials can be simplified to a randomly generated access. Each resource has an identity, a data type, andsupports a set of actions.

REpresentational StateTransfer, or REST, is a design pattern for interacting with resourcesstored in a server. For example, in the request for a multipage result set, the client should include the actual page number to retrieve instead of simply asking for next (see Figure 2). The two concepts are completely orthogonal and independent, but both are central to security design, and the failure to get either one correct increase the chances of compromised system. Spring Boot Tutorials Our Spring Boot tutorials covers the core and advances feature of Spring Boot including Starters, Actuator, CLI and Spring Boot build process.
Ratnesh Prasad 69views. Integrate REST API claims exchanges in your Azure AD B2C user journey to validate user input. Basic authentication works as follows:. HTTP basic authentication. First, download the latest visual studio in your system.
This is free for learning purposes. This serves as a medium of data communication between client and server. We should design REST web - services in a way that in loosely coupled web services , which follow web standards. It should also be development-friendly and flexible enough to be used for a variety of new applications. Secure Web Services ! Only a web client can securely maintain and present its own credentials during Azure AD authentication to acquire an access token.
This article helps you understand commonly used options for securing web services. It also provides instructions on how to perform security configuration settings for a RESTful web service and how to set up authentication against IBM Bluepages enterprise directory and authorization using IBM Bluegroups. You can import your REST service in SoapUI by using WADL files. Besides, SoapUI Pro supports the OpenAPI, Swagger and RAML formats.
When allowing access to data via web services,…security is very important. We want to limit who can view…or even update data. Only trusted individuals should have access. So, how does web service security work?
This passcode is like the key or the token…used to secure a web service. There are many ways to implement authentication in RESTful web services. Representational State Transfer (REST) is an architectural style for designing loosely coupled web services. In this tutorial, I have not used any Jersey specific interceptors and we will see about them in future tutorials.
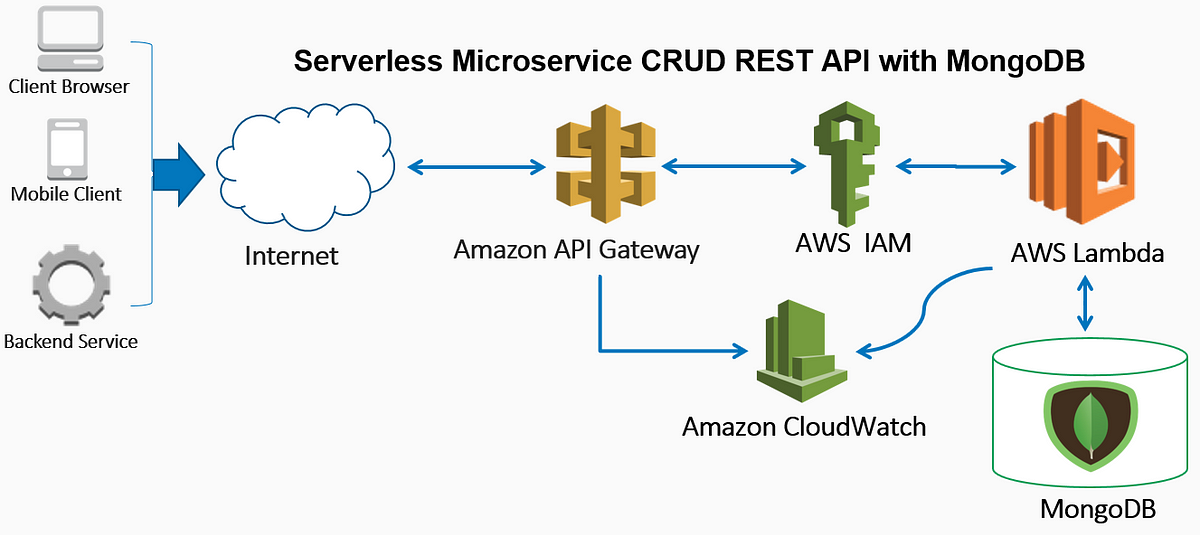
I wanted to build a security layer on top of my WCF RESTful service. Allow the user to auth with the API to get a session key, and. NET makes it easy to build services that reach a broad range of clients, including browsers and mobile devices. NET you use the same framework and patterns to build both web pages and services , side-by-side in the same project.
Even some cloud services such as AWS (Amazon Web Services ) run Node. Now, of course, nothing is quite so clear-cut in the real worl and development communities are always ripe with discussions about which programming language is the best and which environment is the most suitable for a specific.
No comments:
Post a Comment
Note: Only a member of this blog may post a comment.